Please Login to access more options.
|
Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
Problem 1 (The Game Of Scoring)
The game of Scoring is a two-player game. Start by creating a pile of $n\geq 1$ objects (feel free to choose $n$ however you want). On each player's turn, they must choose 1, 2, or 3 items from the pile. Players alternate taking turns until someone takes the last object. Whoever takes the last object wins.
- Play this game several times with various values of $n$.
- For which values of $n$ does the first player have a winning strategy (meaning they are guaranteed to win if they play correctly). Remember to always fully justify your answers.
- For which values of $n$ does the second player have a winning strategy? Why?
- For which values of $n$ does the first player have a winning strategy if we change the rules so that now each player must choose 1, 2, 3, or 4 items from the pile.
- We'll now change the rules and require a player to take anywhere from 1 to $k$ objects each turn. Conjecture the values of $n$ for which the first player has a winning strategy.
Problem 2 (The Game Of Scoring Misere)
A misere game is a game played by the regular rules with one change; whoever wins the game according the regular rules is the loser. Consider again the game of Scoring, but this time we'll play it as a misere game.
- For which values of $n$ does the first player have a winning strategy when playing misere, provided each player must take 1, 2, or 3 objects?
- For which values of $n$ does the first player have a winning strategy when playing misere, provided each player must take 1, 2, 3, or 4 objects?
- If instead a player must take between 1 and $k$ objects, conjecture the values of $n$ for which the first player has a winning strategy when playing misere.
Definition (Encryption Key)
An encryption key is an algorithm which specifies how a message is to be encoded. The encrypted message is often called ciphertext. The original message is called plain text. See Wikipedia for more information.
Definition (Simple Shift Permutation Of The Alphabet)
Let $M$ be a message, which we will think of as a sequence of letters from the standard 26 letter Roman alphabet. We can write $M=(m_1,m_2,m_3, \ldots, m_n)$ where $m_i\in\{a, b, c, \ldots, z\}$. For simplicity, our messages are not case-sensitive and all spaces and punctuation have been removed. To send the phrase "Let's meet at dawn." we'd just use the plain text message $M=(l,e,t,s,m,e,e,t,a,t,d,a,w,n)$.
We now define an encryption key to produce ciphertext from a message $M$. Given a message $M=(m_1,m_2,m_3, \ldots, m_n)$, let $\phi_3(m_i)$ be the letter in the alphabet that has been shifted three right from the current letter. When we hit the end of the alphabet, we'll wrap around so that shifting $z$ right one gets us to $a$. Let's call this the simple shift permutation $\phi_3$. So we now have $\phi_3(a)=d$, $\phi_3(m)=p$, and $\phi_3(z)=c$. In a similar manner, we can define the simple shift permutation $\phi_n$ which shifts each letter right $n$ units.
Problem 3 (First Encryption Key)
Suppose you encounter some ciphertext $(i,q,x,x,p,a,z,q)$ that you know has been encrypted using a simple shift permutation $\phi_n$ for some $n$.
- Decode the ciphertext and state the original message. State the value of $n$ that was used to encode the original message.
- Encode the plain text message "attack at dawn" into ciphertext using the same encryption key you discovered in the first part.
- Are there any other $n$ that would have produced the same results as above? Be ready to fully justify your answer.
Problem 4 (The Set Of Simple Shift Permutations)
Let $S = \{a,b,c,\ldots,z\}$ be the set of letters in the Roman alphabet. For each $n\in\mathbb{Z}$, let $\phi_{n}:S\to S$ represent the encryption key that shifts each letter in the alphabet right $n$, where we wrap around from $z$ to $a$ for letters that need to be shifted past $z$. So $\phi_3(a)=d$, $\phi_3(b)=e$, and $\phi_3(z)=c$. We've called this a simple shift permutation of $S$.
- For which $n$ does $\phi_n$ not change the message?
- Consider the encryption key $\phi_{9}$, which shifts each letter right 9. If a message had been encrypted using $\phi_9$, then clearly $\phi_{-9}$ would decrypt the message as $\phi_{-9}(\phi_9(s))=s$ for any letter $s$. Give a positive integer $n$ that we could also use to decode a message that has been encrypted using $\phi_9$.
- Does $\phi_{30}=\phi_7$? Does $\phi_{33}=\phi_7$? For which $n$ does $\phi_n=\phi_7$? Explain.
- Consider the set of all shifts of $S$, namely $H=\{\phi_n\mid n\in\mathbb{Z}\}$. How many different functions are in $H$? Prove your answer is correct.
Definition (Permutation)
Let $X$ be a set. A $\textdef{permutation}$ of $X$ is a bijection from $X$ to $X$, so it's a function from $X$ into $X$ that is both one-to-one and onto. We can think of a permutation of $X$ as a way of rearranging the elements in $X$. The identity permutation is the permutation $id_X:X\to X$ defined by $id_X(x)=x$.
Problem 5 (Number Of Permutations)
Given finite set $X$ with $n$ elements, how many permutations are there of $X$?
- Show that if $X=\{1\}$, then there is only one permutation of $X$.
- Show that if $X=\{1,2\}$, then there are two permutations of $X$. List them.
- Make a list of all permutations of $X=\{1,2,3\}$, and then of $X=\{1,2,3,4\}$. What pattern do you see?
- Make a conjecture about the number of permutation of $X$ if $|X|=n$. Then prove your conjecture.
Definition (Automorphism Of A Graph)
An $\textdef{automorphism of a graph}$ is a permutation $\sigma$ of the set of vertices such that two vertices $x$ and $y$ form an edge if and only if $\sigma(x)$ and $\sigma(y)$ form an edge. The $\textdef{automorphism group of a graph}$ is the set of all automorphisms of the graph. If $\mathcal{G}$ is a graph, its automorphism group is denoted $\aut(\mathcal{G})$.
Problem 6 (Automorphisms Of A Square)
Consider the graph $\mathcal{G} = (V,E)$ drawn below. The vertex set is $V = \{1,2,3,4\}$ and the set of edges is $$E = \{\{1,2\},\{2,3\},\{3,4\},\{1,4\}\}.$$
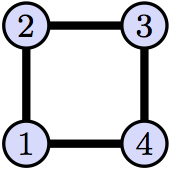
Write down all the automorphisms of $\mathcal{G}$ (there are more than 4, but less than 10). Explain how you know you have listed every automorhpism of $\mathcal{G}$.
This problem continues in AutomorphismsOfASquare2.
Problem 7 (Automorphisms Of A Square 2)
Again consider the graph $\mathcal{G} = (V,E)$ shown below with vertex set $V = \{1,2,3,4\}$ and edges $$E = \{\{1,2\},\{2,3\},\{3,4\},\{1,4\}\}.$$

Recall that set of all automorphisms of $\mathcal{G}$ is written $\aut(\mathcal{G})$. We listed all the elements in this set in problem AutomorphismsOfASquare. Determine if each statement below is true or false. Make sure you justify your answers.
- There is an automorphism $a\in \aut(\mathcal{G})$ such that $a^2=a\circ a$ (the composition) is the identity automorphism, but $a$ is not the identity.
- There is an $a\in \aut(\mathcal{G})$ such that $a^3=a\circ a\circ a$ is the identity but $a$ is not the identity.
- There is an $a\in \aut(\mathcal{G})$ such that every other $b\in \aut(\mathcal{G})$ is of the form $b=a^n$ for some $n$. [Hint: for each element in $\aut(G)$, find the smallest $n$ such that $a^n=id_V$. ]
- For every $a,b\in \aut(\mathcal{G})$, we have $a\circ b = b\circ a$.
Problem 8 (Automorphisms Of A Directed Square)
Consider the directed graph $\mathcal{G} = (V,A)$ shown below with vertex set $V = \{1,2,3,4\}$ and arrows (directed edges) $$A = \{(1,2),(2,3),(3,4),(4,1)\}.$$

- How would you define an automorphism of a directed graph?
- List all the automorphisms of this directed graph. You should have 4.
- Is there is an automorphism $a\in \aut(\mathcal{G})$ such that $a^2=a\circ a$ (the composition) is the identity automorphism, but $a$ is not the identity?
- Is there is an $a\in \aut(\mathcal{G})$ such that $a^3=a\circ a\circ a$ is the identity but $a$ is not the identity?
- Is there is an $a\in \aut(\mathcal{G})$ such that every other $b\in \aut(\mathcal{G})$ is of the form $b=a^n$ for some $n$?
- For every $a,b\in \aut(\mathcal{G})$, do we have $a\circ b = b\circ a$?
Problem 9(Simple Shift Repetition)
Let's now devise a way to not only encrypt a message, but also keep track of who has seen the message? There are several ways to do this. Let's look at an example that involves repeated application of the same encrpytion key. For this example, let's use the encryption key $\phi_4:S\to S$ (the simple shift permutation that shifts right 4).
A group of military commanders decide to send messages using a message chain. The message passes sequentially from one person to the next, where at each stage they apply the encryption key to the ciphertext before sending it on. If I want to send the plain text message $attackatdawn$, then I'd send the message $exxegoexhear$ to the person after me in the chain. This person would decipher the text using $\phi_4^{-1}$ (shift left 4), and then apply $\phi_4$ to the cipher text $exxegoexhear$ and then send the ciphertext $ibbiksibliev$ to the person after them in the chain. This would repeat until the message made it to every commander.
- You receive the cipher text $skkzgzkomnz$. What is the plain text message? How many people have seen this message?
- How many commanders can we include in this encryption scheme and still tell who sent the message?
- If we use $\phi_5$ instead of $\phi_4$, how many commanders can we include in this encryption scheme and still tell who sent the message?
- Is there an encryption key $\phi_n$ so that $\phi_n^2=\phi_0$. In other words, is there an encryption key $\phi_n$ that will only allow up to two commands to be in the chain?
Problem 10 (Cryptography Reading Assignment)
Download the free open source book Abstract Algebra: Theory and Applications by Thomas W. Judson. See http://abstract.ups.edu/. (For a direct link use http://abstract.ups.edu/download/aata-20160809.pdf .)
- Read pages 76-81. This is chapter 7, Introduction to Cryptography. It's OK if you don't understand all the notation.
- Come with at least three questions about parts of the reading you would like to understand more about.
It's OK if you don't understand all of the reading. He uses some theorems and notation that we have not yet covered. If you want to know more about how some of the things worked in the reading, please make sure you ask a question.
Once we have a set of permutations, we'd like to be able to combine them to get new permutations. The previous problem used repetition on simple shift permutations of the alphabet to obtain additional permutations. The next problem has you show that the composition of any finite collection of permutations on a set is always a permutation.
Theorem (The Composition Of Permutations Is A Permutation)
Let $X$ be a set. Suppose that $\sigma_1, \sigma_2, \ldots,\sigma_k$ are permutations of $X$. Then the composition $\sigma_1\circ \sigma_2\circ \ldots\circ \sigma_k$ is a permutation of $X$.
Problem 11 (The Composition Of Permutations Is A Permutation)
Prove theorem (The Composition Of Permutations Is A Permutation). As some reminders, you may use the following facts that you proved in either Math 301 or Math 340. You may use these facts without proof.
- The composition of two injective functions is injective.
- The composition of two surjective functions is surjective.
- A function is a bijection if it is both injective (1 to 1) and surjective (onto). Hence, the composition of two bijective functions is a bijection.
- You might find induction helps you get from a composition of two bijective functions is bijective to the composition of $n$ bijective functions is bijective.
Problem 12 (Do We Need The Associative Law)
In this problem, your job is to explain each step in the process of solving $2x=3$ for $x$. Try to break each part of your computation down into the most basic processes. The only two operations we have on the real numbers are addition and multiplication. Subtraction and division are inverse operations, so rather than saying "divide by 2", you would multiply by the multiplicative inverse of 2. As always, write your solution using complete sentences.
- If you did not use the associative law of multiplication in your work, then go back through your work. It should be there somewhere.
- Did you use the commutative law of multiplication in your work? If you did, make sure you pinpoint where you did. It is possible to solve this problem without the commutative law.
- You might try to justify this as follows:
First divide both sides of $2x=3$ by 2. Then cancel the 2's on the left side of the equation and we have $x=3/2$.
Problem 12 (Simple Matrix Encryption)
Consider the matrix $A = \begin{bmatrix} 2&1&-1\\ 5&2&-3\\ 0&2&1\end{bmatrix}$. Joe decides to send a message to Sam by encrypting the message with the matrix $A$. He first takes his message and converts it to numbers by replacing A with 1, B with 2, C with 3, and so on till replacing Z with 26. He uses a 0 for spaces. After replacing the letters with numbers, he breaks the message up into chunks of 3 letters. He then multiplies each chunk of 3 by the matrix $A$, resulting in a coded message. For example, to send the message "good job ben" he firsts converts the letters to the numbers and places them in a large matrix $M$ (top to bottom, left to right) $$ \left[ \begin{bmatrix}g\\o\\o\end{bmatrix}, \begin{bmatrix}d\\ \ \\ j\end{bmatrix},\begin{bmatrix}o\\b\\\ \end{bmatrix},\begin{bmatrix}b\\e\\n\end{bmatrix}\right] \rightarrow \left[\begin{bmatrix}7\\15\\15\end{bmatrix}, \begin{bmatrix}4\\0\\10\end{bmatrix},\begin{bmatrix}15\\2\\0\end{bmatrix},\begin{bmatrix}2\\5\\14\end{bmatrix}\right] = M= \begin{bmatrix} 7 & 4 & 15 & 2 \\ 15 & 0 & 2 & 5 \\ 15 & 10 & 0 & 14 \end{bmatrix} .$$ To encode the matrix, he computes $$AM = \begin{bmatrix} 14 & -2 & 32 & -5 \\ 20 & -10 & 79 & -22 \\ 45 & 10 & 4 & 24 \end{bmatrix}.$$ and then sends the numbers \([ [ 14, 20, 45], [ -2, -10, 10], [ 32, 79, 4], [ -5, -22, 24] ]\) to Sam. Sam uses the inverse of $A$ to decode the message.
- Use $A^{-1}$ to decode \([ [ 14, 20, 45],[ -2, -10, 10],[ 32, 79, 4],[ -5, -22, 24] ]\) and show the message is "good job ben."
- Decode the message \([[39, 89, 22],[20, 48, 4],[39, 88, 33]]\).
Recall that given a set of vectors $S=\{\vec v_1, \vec v_2,\ldots, \vec v_k\}$, a linear combination of these vectors was a sum of the form $$c_1\vec v_1+c_2\vec v_2+\cdots+c_k\vec v_k.$$ The span of a set of vectors is the set of all linear combinations of the vectors. In linear algebra we took a small set of vectors and spanned the vectors to create vector spaces. We defined the span of $S$ to be the set of all linear combinations of vectors in $S$.
Given a permutation, we've shown that we can use function composition to create new permutations. If $S$ is a set of permutations on $X$, we'd like to have a way to talk about combining the permutations. Instead of multiplying by a scalar and adding, we'll decide how many times to repeatedly apply the function, and then compose different functions together.
Definition (Composition Combination Of Permutations)
Let $X$ be a set, and $S$ be a set of permutations of $X$.
- If $\sigma$ is a permutation of $X$, we'll use exponential notation to express repeated composition of $\sigma$. This gives us $\sigma^2=\sigma\circ \sigma$ and $\sigma^5=\sigma\circ\sigma\circ\sigma\circ\sigma\circ\sigma$, etc.
- We'll use negative exponents when we want to repeated apply an inverse, which gives us $\sigma^{-n}=\left(\sigma^{-1}\right)^n$.
- A composition combination of permutations in $S$ is a composition of the form $$\sigma_1^{n_1}\circ\sigma_2^{n_2}\circ\cdots\circ \sigma_k^{n_k},$$ where $k\in\mathbb{N}$, each $\sigma_i\in S$, and each $n_i\in \mathbb{Z}$ for $i\in \{1,2,3,\ldots,k\}$.
- The span of $S$, written $\text{span}(S)$ is the set of all composition combinations of permutations in $S$. We'll say that the set $S$ generates $\text{span}(S)$.
As an example, if $S=\{a,b,c,d\}$ is a set of permutations of $X$, then the composition $a^2\circ b^{-1}\circ c^3$ is a composition combination of permutations in $S$, and so are $d^{-3}$, $b^5\circ a^{-2}$, and more.
Problem 13 (Simple Shift Repetition Game)
Consider the set of simple shift permutations $H=\{\phi_n\mid n\in \mathbb{Z}\}$ on a 26 letter alphabet. We've shown that there are 26 different functions in this set. Consider the following game.
- The first player picks an element $\sigma_1\in H$. They then remove from $H$ the span of $\sigma_1$ (so everything generated by $\{\sigma_1\}$).
- The second player now chooses an element $\sigma_2\in H$ that hasn't yet been removed. They then remove from $H$ any element in the span of $\{\sigma_1,\sigma_2\}$. At this stage, any permutation that can be written as a composition combination of the permutations $\sigma_1$ and $\sigma_2$ has been removed.
- Players alternate taking turns, choosing an element $\sigma_k\in H$ that hasn't been removed in a previous stage, and then removing from $H$ any element in the span of $\{\sigma_1,\sigma_2,\ldots,\sigma_k\}$.
- Whoever take the last element of $H$ wins. The game can also be played as a misere game.
Answer the following questions.
- Player 1 takes $\phi_6$. Which elements should be removed from $H$
- Is there a way for player 1 to win on the first move? Explain.
- What's the largest number of turns that can occur in this game (so if neither player tries to win, how long can the game go on)?
- If we play this as a misere game, does player 1 have a winning strategy?
Problem 14(The Span Of A Simple Shift)
Suppose that our alphabet $S$ consists of only 12 letters $S=\{a,b,c,d,e,f,g,h,i,j,k,l\}$. Let $H_{12}=\{\phi_n\mid n\in \mathbb{Z}\}$ be the set of simple shift permutations on this 12 letter alphabet (we wrap around from $l$ to $a$).
- For each $n\in \{0,1,2,\ldots,11\}$, list the elements in $\text{span}(\{\phi_n\} ) $.
- For which $n$ does $\text{span}(\{\phi_n\})=H_{12}$.
- Make a conjecture about any patterns you see above and their relation to the size (12) of the alphabet.
- Whenever you make a conjecture, you should always test your conjecture on an example you have not yet considered. Pick another integer $k\neq 12,26$, and look at the set $H_k$ of simple shift permutations of an alphabet consisting of $k$ letters. Then check if your conjecture holds.
Much of our work up to this point has been based on the ability to compute a remainder. This is all based on the Division Algorithm.
Theorem (Division Algorithm)
Let $a,n\in\mathbb{Z}$, with $n> 0$. Then there exists unique integers $q$ and $r$ (called the quotient and remainder) such that $a=qn+r$ where $0\leq r<n$.
Problem 15(Division Algorithm Proof)
Prove the Division algorithm.
One of our main uses of the division algorithm is modular arithmetic.
Definition (Modular Arithmetic)
Let $a,b,n\in \mathbb{Z}$ with $n>0$. We say that two integers $a$ and $b$ are congruent mod $n$, and write $a \mod n= b\mod n$, if they have the same remainder after dividing by $n$. If $a=qn+r$ where $r$ is the remainder after dividing by $n$, then we'll often write $r=a\mod n$. There are lots of ways to denote this in the literature. We might say $r\equiv a\mod n$, $r=a\pmod n$, $a\mod n \equiv b \mod n$, and more.
Problem 16(Remainders Equal Iff Difference Is A Multiple)
Let $a,b,n\in\mathbb{Z}$ with $n>0$. Prove that $a\pmod n = b \pmod n$ if and only if $a-b$ is a multiple of $n$.
Many encryption algorithms depend entirely on modular arithmetic. The RSA public key encryption algorithm requires that we compute extremely large powers of rather large numbers. For example, we might need to compute $2348971^{986871578457358918334698187}$. This can be an expensive operation, unless we find some patterns to help us. The next problem provides a beginning at doing this.
Problem 17(Computing Powers Modn Conjecture)
We need to be able to compute $a^k\pmod n$.
- Compute $2^k\pmod 5$ for $k=1,2,3,4,5,6,7$. What pattern do you see. What is $2^k\pmod 5 $ for $k=257$ and for $k=49827512$.
- Compute $5^k\pmod {11}$ for $k=1,2,3,4,5,6,7,8,9,10,11,12$. Can you discover a pattern. What if $k=3047$ or $k=478209183234$?
- Make a conjecture about $a^k\pmod n$. Come up with a different example to back your conjecture.
We need a common notation to talk about permutations. If $\sigma$ is a permutation of $X=\{1,2,3,4,5,6\}$, then we could use the matrix notation $ \sigma= \begin{bmatrix}1&2&3&4&5&6\\2&4&6&1&5&3\end{bmatrix} $ to represent the permutation $$ \sigma(1)=2,\sigma(2)=4,\sigma(3)=6,\sigma(4)=1,\sigma(5)=5,\sigma(6)=3 $$ Alternately, we could look at cycling patterns that occur in the permutation and write $1\to 2\to 4\to 1$ and then stop because at this point the cycle repeats. We'd also need to write $3\to 6\to 3$ and $5\to 5$, though if we left the $5\to 5$ part off we could assume that 5 did not change. Rather than writing the arrows, we'll represent this permutation by writing $\sigma=(1,2,4)(3,6)(5)$, or leaving off the fact that 5 maps to itself we could just write $\sigma=(1,2,4)(3,6)$. We can use this notation to express any permutation. We need a formal definition for this cycle notation. You can read more about disjoint cycle notation on page 98 in Gallian's Contemporary Abstract Algebra.
Definition (Disjoint Cycle Notation)
Let $X=\{1,2,3,\ldots ,n\}$ for some positive integer $n$. Let $\sigma$ be a permutation which we have written in the matrix form $ \sigma= \begin{bmatrix}1&2&\cdots&n\\\sigma(1)&\sigma(2)&\cdots&\sigma(n)\end{bmatrix}. $ Let $a_1\in X$ (often we choose $a_1=1)$ and then compute $\sigma(a_1),\sigma^2(a_1),\sigma^3(a_n),\ldots, \sigma^{k_1}(a_n)$ until the next application of $\sigma$ returns $a_1$. This gives the first cycle (vector) $\alpha_1=(a_1,\sigma(a_1),\ldots,\sigma^{k_1}(a_1))$. We then pick $a_2\in X$ so that $a_2$ is not an entry in $\alpha_1$, and repeat this process to obtain a second cycle $\alpha_2=(a_2,\sigma(a_2),\sigma^2(a_2),\ldots,\sigma^{k_2}(a_2))$. We then pick $a_3\in X$ so that $a_3$ is not an entry in $\alpha_1$ nor $\alpha_2$, and repeat the process to obtain the cycle $\alpha_3$. At each stage we pick a new element $a_k\in X$ that is not an entry in any of $\alpha_1,\alpha_2,\ldots, \alpha_{k-1}$, and then repeatedly apply $\sigma$ to obtain the cycle $a_k$. The process stops when every element of $X$ is in $\alpha_k$ for some $k$. We then write $$\sigma=\alpha_1\circ\alpha_2\circ\cdots \circ \alpha_m = \alpha_1\alpha_2\cdots\alpha_m$$ where $m$ is the number of cycles needed to represent the permutation. Whether we include the composition symbol or not is a matter of preference.
We will often omit writing singleton vectors $(a)$. So if $X=\{1,2,3,4\}$, then instead of writing $(1)(2,3)(4)$, we'll just write $(2,3)$. The permutation $(2,3)$ does not change the elements $1$ and $4$, so we omit writing them. The identity permutation would be $(1)(2)(3)(4)$. We could omit all singletons which would leave us with nothing, so in this case we'll write $()$ to represent the identity permutation.
Problem 18(Disjoint Cycle Notation Practice With Automorphisms Of A Square)
We have already shown that there are 8 automorphisms of the graph below.

Write each of these automorphism using disjoint cycle notation. As an example, the automorphism that leaves 1 and 3 unchanged, but swaps 2 and 4, we write as $(1)(2,4)(3)$.
Problem 19(Automorphisms On Several Graphs With 4 Vertices)
Consider the two graphs below.
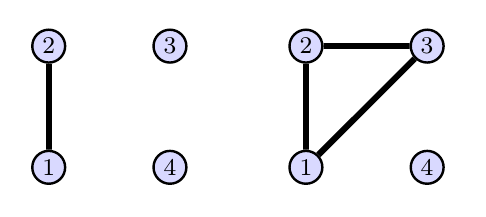
- For each graph, list the automorphisms of the graph. Use disjoint cycle notation to represent each automorphism.
- For each automorphism, state the smallest positive value of $k$ for which $\sigma^k$ is the identity automorphism. This is called the order of the automorphism.
- Construct another graph on 4 vertices different than the three we have seen so far. How many automorphisms does this graph have? Explain.
Definition (The Order Of A Permutation)
The order of a permutation $\sigma$ is the smallest positive integer $n$ such that $\sigma^n$ equals the identity permutation.
Definition (The Game of Permutation Scoring also called Generate/Don't Generate)
Just as in the Simple Shift Repetition Game, we can play a similar game with any set of permutations of the same set $X$. Let $H$ be a set of permutations of a set $X$. We'll generally assume that the set $X$ is finite so that the game is guaranteed to end. However, you can play this game with an infinite set $X$.
Here are the rules.
- The first player picks an element $\sigma_1\in H$. They then remove from $H$ the span of $\{\sigma_1\}$ (so everything generated by $\sigma_1$).
- The second player now chooses an element $\sigma_2\in H$ that hasn't yet been removed. They then remove from $H$ any element in the span of $\{\sigma_1,\sigma_2\}$. At this stage, any permutation that can be written as a composition combination of the permutations $\sigma_1$ and $\sigma_2$ has been removed.
- Players alternate taking turns, choosing an element $\sigma_k\in H$ that hasn't been removed in a previous stage, and then removing from $H$ any element in the span of $\{\sigma_1,\sigma_2,\ldots,\sigma_k\}$.
- Whoever takes the last element of $H$ wins.
There are several variations:
- The game can also be played as a misere game, where whoever takes the last element of $H$ wins.
- You win by taking the last element. However, you cannot take the last element unless there are no other legal choices. So you can't try to win, rather you must be forced to win.
Problem 20(The Game Of Permutation Scoring On A Square)
Let's play the game of scoring on the automorphism group of the square. We know there are 8 automorphism. Play this game a few times to get a feel for what different choices will give.
- Show there is no way for player 1 to win on the first move.
- If player 1 takes any of the flips for their first move, what should player 2 choose to win the game?
- Does player 1 have a winning strategy? What is it?
It would be nice if we could create a way to visually keeping track of which elements of $H$ have been taken. Let me describe how we can do this with an example. Suppose you are playing the game on a square (as above). Player one takes the permutation $(1,2,3,4)$. Then player $2$ chooses the element $(1,2)(3,4)$. Here's how we make the graph.
- Each element in $H$ will represent a vertex.
- When player 1 chooses $(1,2,3,4)$, pick a color (I'll choose red) and then draw a red arrow from each permutation $\sigma\in H$ to the permutation $(1,2,3,4)\circ \sigma$. In other words, we're going to draw a graph that shows what happens if we apply the automorphism $(1,2,3,4)$ after doing any other automorphism. If we start at the identity permutation $()=(1)(2)(3)(4)$, then we have $(1,2,3,4)\circ ()=(1,2,3,4)$, so we draw a red arrow from $()$ to $(1,2,3,4)$. Similarly, starting at $(1,2,3,4)$ we draw an arrow to $(1,2,3,4)\circ(1,2,3,4)=(1,3)(2,4)$. Continuing in this fashion for each permutation gives us the graph below, with two red cycles of 4.
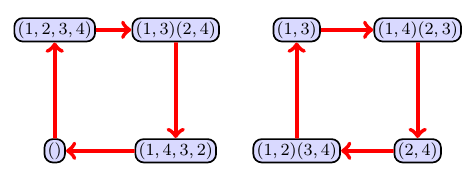
- The elements that are removed after choosing $(1,2,3,4)$ are any elements that we can get to by following a path that contains $(1,2,3,4)$. These are the 4 automorphisms in the cycle on the left.
- Now player 2 chooses $(1,2)(3,4)$. We now use a different color (I chose blue in the example below), and then at each vertex draw an arrow starting at $\sigma\in H$ and ending at $(1,2)(3,4)\circ \sigma$. The tricky part is finding a nice way to draw the graph without to many edge crossings (do you see how the outer circle flipped directions). Both of the examples below are ways to represent this graph. We can use an edge with an arrow on each end to illustrate that there is an arrow going both ways.
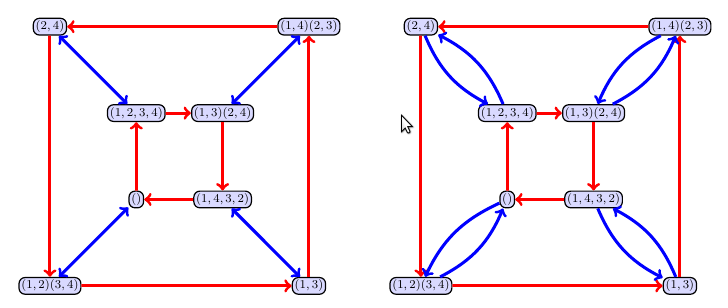
- The arrows in the graph above represent composition by either $(1,2,3,4)$ or $(1,2)(3,4)$. If you start at $(1,3)$ and want to compute $(1,2,3,4)\circ(1,2)(3,4)\circ(1,3)$, then you just have to start at $(1,3)$, follow the blue arrow to get to $(1,2)(3,4)\circ(1,3)=(1,4,3,2)$, and then follow the red arrow to get to $(1,2,3,4)\circ(1,4,3,2)$.
The mathematical program Sage can also help with the computations. The command PermutationGroup() below creates the span of the permutations listed. The command cayley_graph() creates the graph described above, but only shows the part of the graph that contains the permutations listed. Try executing the block of code below.
g1 = PermutationGroup(["(1,2,3,4)"]) #The set g1 is the span of the permutations listed. d1=g1.cayley_graph() #This creates the Cayley graph of the g1. d1.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) #This shows the Cayley graph. print(g1.list()) #This print a list of the elements in g1. g2 = PermutationGroup(["(1,2,3,4)", "(1,2)(3,4)"]) d2=g2.cayley_graph() d2.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g2.list())
Problem 21 (Composing Permutations Using Disjoint Cycle Notation)
Let $R_{90}=(1,2,3,4)$ and $H=(1,2)(3,4)$.
- Express the compositions $R_{90}\circ H$ and $H\circ R_{90}$ in cycle notation. Be prepared to explain how you computed this.
- Express the compositions $R_{90}\circ (1,3)$ and $H\circ (1,3)$ in cycle notation. Can you see these products in the graph above?
- Express the composition $(1,2,4)\circ (1,4)(2,3)\circ (2,4)$ in cycle notation. Note that $(1,2,4)$ is not an automorphism of the square, but is a permutation.
- Evalute the Sage command below. In the second graph below you should see that starting at $()$ and following the colored arrows corresponding to $(2,4)$ and then $(1,4)(2,3)$ gets you to the element $(1,4,3,2)$ which is precisely the composition $(1,4)(2,3)\circ (2,4)$. In the third graph below, if you start at the identity $()$ and the follow the colored arrow corresponding to $ (2,4)$, and then $(1,4)(2,3)$, and then $(1,2,4)$, you should end up at the same spot as you did in part 3. Click evaluate again if the graph you have is hard to read (as the graph will redraw).
g1 = PermutationGroup(["(2,4)"]) #The set g1 is the span of the permutations listed. d1=g1.cayley_graph() #This creates the Cayley graph of the g1. d1.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) #This shows the Cayley graph. print(g1.list()) #This print a list of the elements in g1. g2 = PermutationGroup(["(2,4)","(1,4)(2,3)"]) d2=g2.cayley_graph() d2.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g2.list()) g3 = PermutationGroup(["(2,4)","(1,4)(2,3)", "(1,2,4)"]) d3=g3.cayley_graph() d3.show(color_by_label=True, vertex_size=0.03, vertex_labels=True,figsize=8) print(g3.list())
Problem 22 (Creating Cayley Graphs Of Simple Shift Permutations)
Let's make some Cayley graphs as they relate with the game of Scoring on simple shift permutations. To get Sage to make the graphs, you'll first have to write the simple shift permutation in disjoint cycle notation. As an example, if there are 6 letters in our alphabet $X=\{1,2,3,4,5,6\}$, then we could write the simple shift $\phi_2$ as $(2,4,6)(1,3,5)$. If player 1 chooses $\sigma_1=\phi_2$ and player 2 chooses $\sigma_2=\phi_3$, then the following Sage code visually provides a graph of $\text{span}(\{\sigma_1\})$ and then $\text{span}(\{\sigma_1,\sigma_2\})$.
g1 = PermutationGroup(["(2,4,6)(1,3,5)"]) d1=g1.cayley_graph() d1.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g1.list()) g2 = PermutationGroup(["(2,4,6)(1,3,5)","(1,4)(2,5)(3,6)"]) d2=g2.cayley_graph() d2.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g2.list())
By hand, my first graph would contain two unconnected triangles. My second graph would look similar to the graph above.
- Suppose the alphabet is $X=\{1,2,3,4,5,6\}$. Player 1 chooses $\phi_1$. Draw the associated graph.
- Suppose the alphabet is $X=\{1,2,\ldots,10\}$. Player 1 chooses $\phi_5$. Player 2 chooses $\phi_4$. Draw the two associated graphs.
- Suppose the alphabet is $X=\{1,2,\ldots,12\}$. Player 1 chooses $\phi_5$. Draw the associated graph.
- Suppose the alphabet is $X=\{1,2,\ldots,12\}$. Player 1 chooses $\phi_6$. Player 2 chooses $\phi_2$. Player 1 then chooses $\phi_3$. Draw the three associated graphs. The first graph should consist of 6 arrows between pairs of vertices (Sage will only show you the segment connnecting $()$ and $\phi_6$). Your second graph should have 2 hexagons with arrows crossing in the middle. The last graph should connect the edges of the hexagons.
Here's a blank Sage cell that you can use to perform some computations. You'll probably want to copy code from above and make some changes.
When we create graphs with Sage, it always creates a graph of the span of the permutations given. These graphs have a lot of really nice symmetry properties, and these properties are central to abstract algebra.
Problem 23 (Permutation Scoring On S 3)
Consider the game of permutation scoring on the set $S_3$, where $S_3$ represents the set of all permutations of $X=\{1,2,3\}$. We already know that there are 6 elements in $S_3$.
- Play the game of permutation scoring on $S_3$. Play it a few times.
- Can player 1 win by choosing a single permutation in $S_3$?
- Does player $1$ have a winning strategy? What is it?
- Pick an element in $S_3$ other than the identity, and call it $\sigma$. Let $S=\text{span}(\sigma)$. What is the span of $S$?
- Repeat part 4 with a different element of $S_3$. You can use Sage to make this part fast (first compute the span of $\sigma$ with Sage. The list below the graph gives you the elements of the span. Then create a graph using these elements.
- Make a conjecture.
Definition (A Closed Set Of Permutations)
We say that a set of permutations is closed if the set $S$ is equal to its span, so notionally we write $$S=\text{span}{(S)}.$$ In other words, we say that $S$ is closed if the set $S$ already contains every composition combination of permutations of elements in $S$.
Problem 24 (The Span Of A Set Of Permutations Is Closed)
Let $S$ be a set of permutations of $X$. Show that $\text{span}(S)$ is closed. In other words, show that once you form the span of a set $S$ of permutations of $X$, you cannot obtain any new permutations by spanning the span. For this reason, we'll often refer to $\text{span}(S)$ as the closure of $S$.
Definition (The Order Of A Permutation)
The order of a permutation $\sigma$ is the smallest positive integer $n$ such that $\sigma^n$ equals the identity permutation.
Definition (The Game of Permutation Scoring also called Generate/Don't Generate)
Just as in the Simple Shift Repetition Game, we can play a similar game with any set of permutations of the same set $X$. Let $H$ be a set of permutations of a set $X$. We'll generally assume that the set $X$ is finite so that the game is guaranteed to end. However, you can play this game with an infinite set $X$.
Here are the rules.
- The first player picks an element $\sigma_1\in H$. They then remove from $H$ the span of $\{\sigma_1\}$ (so everything generated by $\sigma_1$).
- The second player now chooses an element $\sigma_2\in H$ that hasn't yet been removed. They then remove from $H$ any element in the span of $\{\sigma_1,\sigma_2\}$. At this stage, any permutation that can be written as a composition combination of the permutations $\sigma_1$ and $\sigma_2$ has been removed.
- Players alternate taking turns, choosing an element $\sigma_k\in H$ that hasn't been removed in a previous stage, and then removing from $H$ any element in the span of $\{\sigma_1,\sigma_2,\ldots,\sigma_k\}$.
- Whoever takes the last element of $H$ wins.
There are several variations:
- The game can also be played as a misere game, where whoever takes the last element of $H$ wins.
- You win by taking the last element. However, you cannot take the last element unless there are no other legal choices. So you can't try to win, rather you must be forced to win.
Problem 20(The Game Of Permutation Scoring On A Square)
Let's play the game of scoring on the automorphism group of the square. We know there are 8 automorphism. Play this game a few times to get a feel for what different choices will give.
- Show there is no way for player 1 to win on the first move.
- If player 1 takes any of the flips for their first move, what should player 2 choose to win the game?
- Does player 1 have a winning strategy? What is it?
It would be nice if we could create a way to visually keeping track of which elements of $H$ have been taken. Let me describe how we can do this with an example. Suppose you are playing the game on a square (as above). Player one takes the permutation $(1,2,3,4)$. Then player $2$ chooses the element $(1,2)(3,4)$. Here's how we make the graph.
- Each element in $H$ will represent a vertex.
- When player 1 chooses $(1,2,3,4)$, pick a color (I'll choose red) and then draw a red arrow from each permutation $\sigma\in H$ to the permutation $(1,2,3,4)\circ \sigma$. In other words, we're going to draw a graph that shows what happens if we apply the automorphism $(1,2,3,4)$ after doing any other automorphism. If we start at the identity permutation $()=(1)(2)(3)(4)$, then we have $(1,2,3,4)\circ ()=(1,2,3,4)$, so we draw a red arrow from $()$ to $(1,2,3,4)$. Similarly, starting at $(1,2,3,4)$ we draw an arrow to $(1,2,3,4)\circ(1,2,3,4)=(1,3)(2,4)$. Continuing in this fashion for each permutation gives us the graph below, with two red cycles of 4.

- The elements that are removed after choosing $(1,2,3,4)$ are any elements that we can get to by following a path that contains $(1,2,3,4)$. These are the 4 automorphisms in the cycle on the left.
- Now player 2 chooses $(1,2)(3,4)$. We now use a different color (I chose blue in the example below), and then at each vertex draw an arrow starting at $\sigma\in H$ and ending at $(1,2)(3,4)\circ \sigma$. The tricky part is finding a nice way to draw the graph without to many edge crossings (do you see how the outer circle flipped directions). Both of the examples below are ways to represent this graph. We can use an edge with an arrow on each end to illustrate that there is an arrow going both ways.

- The arrows in the graph above represent composition by either $(1,2,3,4)$ or $(1,2)(3,4)$. If you start at $(1,3)$ and want to compute $(1,2,3,4)\circ(1,2)(3,4)\circ(1,3)$, then you just have to start at $(1,3)$, follow the blue arrow to get to $(1,2)(3,4)\circ(1,3)=(1,4,3,2)$, and then follow the red arrow to get to $(1,2,3,4)\circ(1,4,3,2)$.
The mathematical program Sage can also help with the computations. The command PermutationGroup() below creates the span of the permutations listed. The command cayley_graph() creates the graph described above, but only shows the part of the graph that contains the permutations listed. Try executing the block of code below.
g1 = PermutationGroup(["(1,2,3,4)"]) #The set g1 is the span of the permutations listed. d1=g1.cayley_graph() #This creates the Cayley graph of the g1. d1.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) #This shows the Cayley graph. print(g1.list()) #This print a list of the elements in g1. g2 = PermutationGroup(["(1,2,3,4)", "(1,2)(3,4)"]) d2=g2.cayley_graph() d2.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g2.list())
Problem 21 (Composing Permutations Using Disjoint Cycle Notation)
Let $R_{90}=(1,2,3,4)$ and $H=(1,2)(3,4)$.
- Express the compositions $R_{90}\circ H$ and $H\circ R_{90}$ in cycle notation. Be prepared to explain how you computed this.
- Express the compositions $R_{90}\circ (1,3)$ and $H\circ (1,3)$ in cycle notation. Can you see these products in the graph above?
- Express the composition $(1,2,4)\circ (1,4)(2,3)\circ (2,4)$ in cycle notation. Note that $(1,2,4)$ is not an automorphism of the square, but is a permutation.
- Evalute the Sage command below. In the second graph below you should see that starting at $()$ and following the colored arrows corresponding to $(2,4)$ and then $(1,4)(2,3)$ gets you to the element $(1,4,3,2)$ which is precisely the composition $(1,4)(2,3)\circ (2,4)$. In the third graph below, if you start at the identity $()$ and the follow the colored arrow corresponding to $ (2,4)$, and then $(1,4)(2,3)$, and then $(1,2,4)$, you should end up at the same spot as you did in part 3. Click evaluate again if the graph you have is hard to read (as the graph will redraw).
g1 = PermutationGroup(["(2,4)"]) #The set g1 is the span of the permutations listed. d1=g1.cayley_graph() #This creates the Cayley graph of the g1. d1.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) #This shows the Cayley graph. print(g1.list()) #This print a list of the elements in g1. g2 = PermutationGroup(["(2,4)","(1,4)(2,3)"]) d2=g2.cayley_graph() d2.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g2.list()) g3 = PermutationGroup(["(2,4)","(1,4)(2,3)", "(1,2,4)"]) d3=g3.cayley_graph() d3.show(color_by_label=True, vertex_size=0.03, vertex_labels=True,figsize=8) print(g3.list())
Problem 22 (Creating Cayley Graphs Of Simple Shift Permutations)
Let's make some Cayley graphs as they relate with the game of Scoring on simple shift permutations. To get Sage to make the graphs, you'll first have to write the simple shift permutation in disjoint cycle notation. As an example, if there are 6 letters in our alphabet $X=\{1,2,3,4,5,6\}$, then we could write the simple shift $\phi_2$ as $(2,4,6)(1,3,5)$. If player 1 chooses $\sigma_1=\phi_2$ and player 2 chooses $\sigma_2=\phi_3$, then the following Sage code visually provides a graph of $\text{span}(\{\sigma_1\})$ and then $\text{span}(\{\sigma_1,\sigma_2\})$.
g1 = PermutationGroup(["(2,4,6)(1,3,5)"]) d1=g1.cayley_graph() d1.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g1.list()) g2 = PermutationGroup(["(2,4,6)(1,3,5)","(1,4)(2,5)(3,6)"]) d2=g2.cayley_graph() d2.show(color_by_label=True, vertex_size=0.03, vertex_labels=True) print(g2.list())
By hand, my first graph would contain two unconnected triangles. My second graph would look similar to the graph above.
- Suppose the alphabet is $X=\{1,2,3,4,5,6\}$. Player 1 chooses $\phi_1$. Draw the associated graph.
- Suppose the alphabet is $X=\{1,2,\ldots,10\}$. Player 1 chooses $\phi_5$. Player 2 chooses $\phi_4$. Draw the two associated graphs.
- Suppose the alphabet is $X=\{1,2,\ldots,12\}$. Player 1 chooses $\phi_5$. Draw the associated graph.
- Suppose the alphabet is $X=\{1,2,\ldots,12\}$. Player 1 chooses $\phi_6$. Player 2 chooses $\phi_2$. Player 1 then chooses $\phi_3$. Draw the three associated graphs. The first graph should consist of 6 arrows between pairs of vertices (Sage will only show you the segment connnecting $()$ and $\phi_6$). Your second graph should have 2 hexagons with arrows crossing in the middle. The last graph should connect the edges of the hexagons.
Here's a blank Sage cell that you can use to perform some computations. You'll probably want to copy code from above and make some changes.
When we create graphs with Sage, it always creates a graph of the span of the permutations given. These graphs have a lot of really nice symmetry properties, and these properties are central to abstract algebra.
Problem 23 (Permutation Scoring On S 3)
Consider the game of permutation scoring on the set $S_3$, where $S_3$ represents the set of all permutations of $X=\{1,2,3\}$. We already know that there are 6 elements in $S_3$.
- Play the game of permutation scoring on $S_3$. Play it a few times.
- Can player 1 win by choosing a single permutation in $S_3$?
- Does player $1$ have a winning strategy? What is it?
- Pick an element in $S_3$ other than the identity, and call it $\sigma$. Let $S=\text{span}(\sigma)$. What is the span of $S$?
- Repeat part 4 with a different element of $S_3$. You can use Sage to make this part fast (first compute the span of $\sigma$ with Sage. The list below the graph gives you the elements of the span. Then create a graph using these elements.
- Make a conjecture.
Definition (A Closed Set Of Permutations)
We say that a set of permutations is closed if the set $S$ is equal to its span, so notionally we write $$S=\text{span}{(S)}.$$ In other words, we say that $S$ is closed if the set $S$ already contains every composition combination of permutations of elements in $S$.
Problem 24 (The Span Of A Set Of Permutations Is Closed)
Let $S$ be a set of permutations of $X$. Show that $\text{span}(S)$ is closed. In other words, show that once you form the span of a set $S$ of permutations of $X$, you cannot obtain any new permutations by spanning the span. For this reason, we'll often refer to $\text{span}(S)$ as the closure of $S$.
We'll be using modular arithmetic in a lot of things that we do throughout the semester. Let's invent a notation to help us talk about modular arithmetic.
Definition (The Set ZN Of Integers Mod N)
For each positive integer $n$, let $\mathbb{Z}_n=\{0,1,2,\ldots, n-1\}$ which is the same as $\mathbb{Z}_n = \{k\mod n\mid k\in \mathbb{Z}\}$. This is just the set of remainders when dividing by $n$. We'll refer to them as the integers modulo $n$, or the integers mod $n$.
Question
Take a look at the last question of The Set Of Simple Shift Permutations. Does this definition look familiar?
In previous problems, we've been using without proof some facts about modular arithmetic, namely that we can perform addition and subtraction either before or after we compute a remainder. Let's prove this is true.
Problem 25 (Modular Arithmetic Properties)
Let $n$ be a positive integer. Let $a,b\in \mathbb{Z}$.
- Show that $((a \mod n)+(b\mod n))\mod n = (a+b)\mod n$. In other words, show that the sum of the remainders has the same remainder as the original sum.
- Show that $((a \mod n)(b\mod n))\mod n = (ab)\mod n$. In other words, show that the product of the remainders has the same remainder as the original product.
Remember, you'll want to use the division algorithm to obtain quotient and remainders when dividing $a$, $b$, $ab$, and $a+b$ by $n$. You'll need to use the problem, Remainders Equal Iff Difference Is A Multiple, to complete your work.
Problem 26 (Powers With Modular Arithmetic)
- We know that $481\mod {483} =(-2)\mod {483}$. Use this fact to quickly compute $481^2\mod{483}$ without a calculator. [How can you use the $-2$ to simplify this?]
- Using the same idea, what is $481^{3}\mod{483}$ and $481^4\mod{483}$? You should be giving a positive integer less than 483 for all your answers.
- Explain why $12\cdot 16 \mod 17$ is the same as $(-5)(-1)\mod 17$.
- Now compute $14^k \pmod {17}$ without a calculator for as many values of $k$ as needed until you find a repeating pattern. See the hint below.
Let me give you a suggestion. Rather than trying to compute $14^4$, instead first compute $14^2$ by considering $(-3)^2$. To compute $(14)^3$, instead use the product $(14)^2(14)=(9)(-3)=(-8)(-3)$. Use your work from the previous power to figure out the next power. If you try to do this with brute force, it gets outrageously large really fast. If you swap from positive to negative values when the numbers get large (above 8), you should be able to do this without ever needing long division. You should find that no product ever gets above 24.
The following Sage code will compute powers with modular arithmetic. You are welcome to check your answers with this, but the whole point to the problem is to learn how to simplify the computations by hand. To compute $a^m\mod n$ you would write "power_mod($a$,$m$,$n$)."
power_mod(481, 4, 483)
Problem 27 (Matrix Encryption Mod 5)
In the Problem (Simple Matrix Encryption), we took a plain text message written in columns of a matrix $M$ and a matrix $A$ and used the product $AM$ to encode a message. Let's now combine matrix encryption with modular arithmetic to obtain a new encryption scheme. Once we have done this, we'll be one step closer to understanding modern encryption techniques. To simplify our work, let's use a small alphabet consisting of 5 letters. Instead of using the set $S=\{a,b,c,d,e\}$, let's just use numbers for our letters and we'll consider the alphabet $S=\{0,1,2,3,4\}=\mathbb{Z}_5$. Given the plain text "bad bed" or "10 31 43", we can encode it in the columns of the matrix $$M=\begin{bmatrix}1&3&4\\0&1&3\end{bmatrix}.$$ An 2 by 2 encryption key using coefficients mod 5 is a 2 by 2 matrix $A=\begin{bmatrix}a&b\\c&d\end{bmatrix}$ where $a,b,c,d\in \mathbb{Z}_5$. Here are the steps to our encryption scheme.
- First convert the plain text to a matrix $M$ where the letters are place in the matrix top to bottom, column by column.
- Take the encryption key $A$ and compute the product $AM$.
- Reduce all the entries in $AM$ mod 5. So the cipher text only consists of the numbers in $\mathbb{Z}_5$.
Answer the following questions.
- Suppose we let $A=\begin{bmatrix}4&2\\1&3\end{bmatrix}$. Why is this matrix not suitable as an encryption key? (Hint: what is the determinant, and why is that a problem?)
- Suppose we let $A=\begin{bmatrix}2&1\\4&3\end{bmatrix}$. The inverse of $A$ if we ignore modular arithmetic is $\frac{1}{2}\begin{bmatrix}3&-1\\-4&2\end{bmatrix}$. We know that we can replace $-4$ with $1$ when working modular 5. Similarly we can replace $-1$ with a positive number. We need to find the multiplicative inverse of 2 when working modular 5. Find a value $b\in \mathbb{Z}_5$ so that $2b\mod 5=1$. This number $b$ is the inverse of $2$ modular 5.
- State a matrix $B$ with coefficients in $\mathbb{Z}_5$ so that $AB$ is the identity matrix after reducing each entry mod 5. Actually perform the product by hand, and show how this matrix product reduces to the identity.
Definition (Modular Multiplicative Inverse and $U(n)$)
Let $n$ be a positive integer, and let $a\in \mathbb{Z}_n$. Then the modular multiplicative inverse of $a \mod n$ is an integer $b\in \mathbb{Z}_n$ such that $(ab)\mod n=1$. If such an integer exists, then we'll write $a^{-1}\mod n$ to represent the modular multiplicative inverse. If the context is clear, we may just refer to this as the inverse instead of the modular multiplicative inverse. We'll use the notation $U(n)$ to represent the set of elements in $\mathbb{Z}$ that have a modular multiplicative inverse. Notationaly, we write $$U(n)=\{a\in\mathbb{Z}_n\mid \text{ there exists } b\in \mathbb{Z}_n \text{ such that } (ab)\mod n=1\}.$$
The Sage code "inverse_mod(a,n)" will compute the modular multiplicative inverse of $a\mod n$ or return an error.
inverse_mod(7, 11)
Problem 28 (Computing Multiplicative Inverses For Small N)
To use modular arithmetic in matrix encryption, we must be able to find the modular multiplicative inverse of $a \mod n$. For each $n\leq 13$ and $a\in \mathbb{Z}_n$, we now compute the inverse of $a\mod n$ or explain why it does not have one.
- Why does $0\mod n$ never have an inverse?
- What is the multiplicative inverse of $1\mod n$?
- For $n=3$, what is the multiplicative inverse of $a=2$.
- For $n=4$, show that 2 does not have an inverse by computing $2\cdot 0$, $2\cdot 1$, $2\cdot 2$, and $2\cdot 3$ all modulo $4$. What is $3^{-1}\mod 4$?
- For each $n$ between 5 and 13, create a table that shows the inverse of each $a\in \mathbb{Z}_n$. List the elements of $\mathbb{Z}_n$ along the top row, and beneath each element list the multiplicative inverse, or cross off the number if there is no multiplicative inverse.
When you are done you should have a list of the elements of $U(n)$ for each $n$ up to 13, as well as the inverse of each element in $U(n)$. Do you see any patterns?
For $n=9$, you should obtain a table somewhat similar to the following table.
| $a$ | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| $a^{-1}$ | x | 1 | 5 | x | 7 | 2 | x | 4 | 8 |
Definition (Cayley Graph Of A Span Of Permutations)
Let $X$ be a set. Let $S$ be a set of permutations of $X$. Then a Cayley graph of $H=\text{span} (S)$ generated by $S$, which we'll write as $(H,S)$, is a colored directed graph that satisfies the the following three properties:
- The vertex set is $\text{span} (S)$. Each vertex corresponds to a permutation.
- Each element $s \in S$ is assigned a unique color which we'll denote by $c_s$.
- For each color $c_s$, and each vertex $\sigma$, we draw the colored arrow $(\sigma ,s \circ \sigma)$.
Most of the time we assume that $S$ does not contain the identity. However, if it does contain the identity, then we just draw a colored loop $(\sigma,\sigma)$ at each vertex.
Problem 29 (Cayley Graph Patterns)
In each scenario below, you should draw a Cayley graph.
- Let $X=\mathbb{Z}$, an infinite set. Consider the permutation $\phi_1:\mathbb{Z}\to \mathbb{Z}$ defined by $\phi_1(x)=x+1$. This permutation shifts elements in $\mathbb{Z}$ right one, with no wrap around. If we let $S=\{\phi_1\}$, give a rough sketch of the Cayley graph of $\text{span}(S)$. It's a rough sketch of the graph because there are infinitely many vertices.
- How would you change your graph in part 1 if instead you used $S=\{\phi_2,\phi_3\}$, where these are shifts right 2 and 3 respectively?
- Suppose that $X$ is a set, and that $S$ contains a single automorphism $s$ of $X$. Suppose also that we know $s^6$ is the identity (so following the arrow colored $c_s$ 6 times will return us to where we started). Construct a Cayley graph of $\text{span}(S)$. Is there more than one right answer to this?
- Suppose that we know $S$ contains two elements $a$ and $b$. We also know that $a^2$ and $b^4$ are both the identity. In addition, we know that $a\circ b=b\circ a$, so if we start somewhere and follow the arrows colored $c_a$ and then $c_b$, then we should end up at the same place if we followed the arrows colored $c_b$ and then $c_a$. Construct a graph that satisfies these relationships. We'll often write this as $$\left<a,b\mid a^2=id, b^4=id, a\circ b=b\circ a\right>.$$
For more problems, see AllProblems
